

The Journey of News Direct
News Direct’s genesis lies in the fusion of deep industry experience with cutting-edge tech. We’re redefining news distribution for the digital era.
Innovative and interactive platform
Our platform offers a unique blend of technology and customization. Dive into a world of intuitive design, featuring compelling visuals, interactive elements, and seamless navigation.
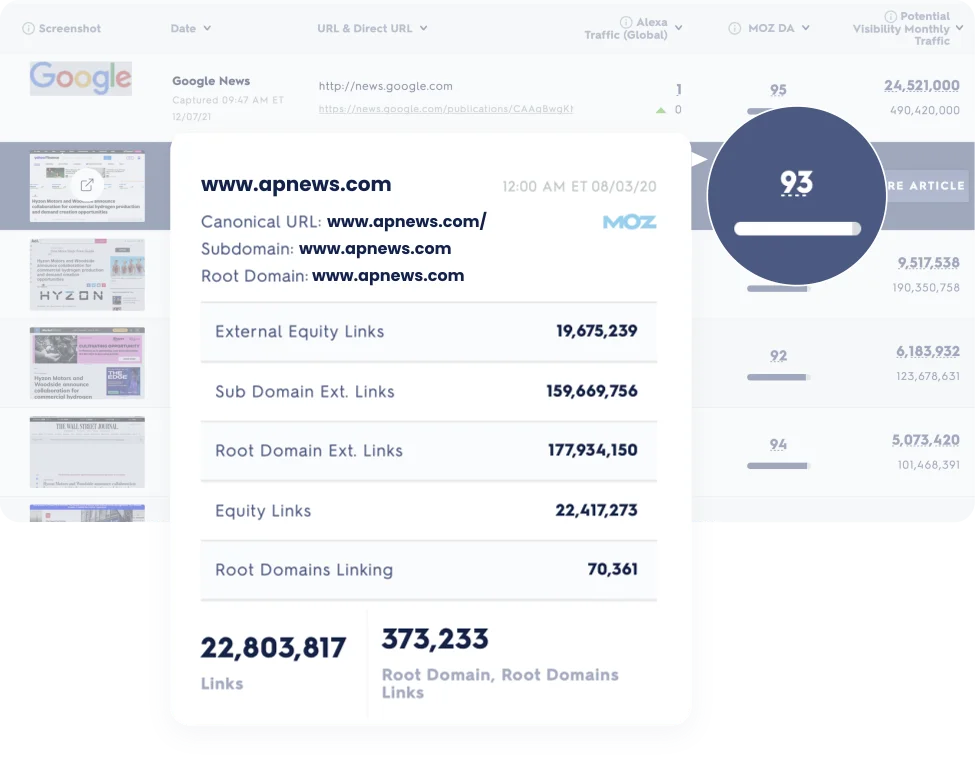
Efficiency and support, reimagined. Access 24/7 expert support and exclusive features like SimpliFi™ for quick and secure earnings releases.
Control and creativity at your fingertips. Enjoy unmatched flexibility and security. Our studio supports seamless logo, image, and video integration, backed by robust version control.
Stand out with Digital Asset Direct™. Distribute engaging multimedia content directly. Break through the clutter with captivating formats and straightforward uploading.

The Journey of News Direct
Your content’s security is paramount. Rely on our two-factor authentication and cloud isolation technology for ultimate protection.
Expand your influence with our extensive media network. Benefit from customizable geographic targeting and premium site postings.

Track and measure your impact with our advanced analytics. Gain actionable insights to refine your strategy and maximize reach.
From broadcast media partnerships to robust media databases, amplify your narrative with our suite of synergistic services.

Enjoy a seamless experience across all devices. Our mobile-responsive design ensures your content is always accessible and engaging.

